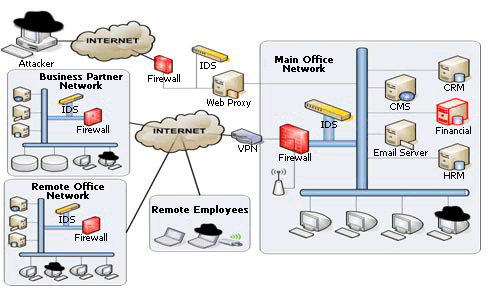
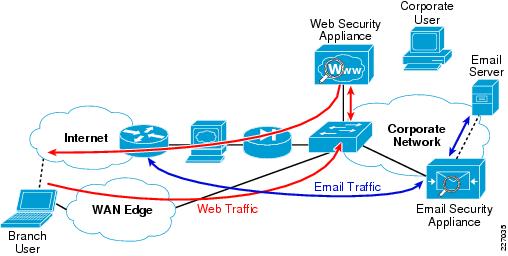
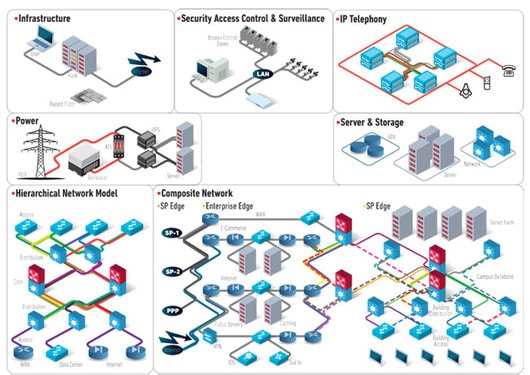
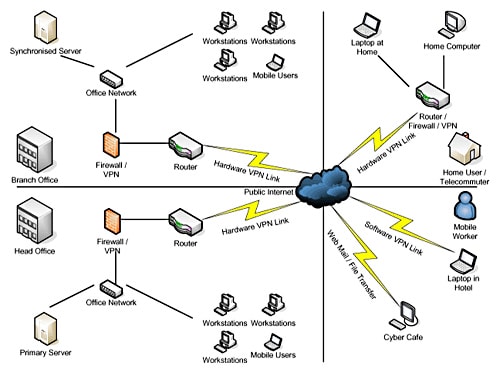
Designing and Implementing IT Security Infrastructure
Introduction Bruce Schneier, the renowned security technologist and author, said that the mantra for any good security engineer is “Security is not merely a product, but a process. It's more than designing strong cryptography into a system; it's designing the fail-safe system such that, all security measures, including cryptography, work together." After having worked as a system/network administrator for couple of years, I was instrumental in the design and implementation of my organization’s System Networking and Communication Infrastructure. I had been given the responsibility for the installation, improvement and maintenance of security of the entire Information Technology Infrastructure of the organization. During this period, I realized the need for acquiring a high level of understanding of the critical issues of security and implementing the same in a real life network and system environment. While reviewing various papers and books on security, and some security breach incidents, I realized that that there are not many resources available that provide a stepby-step approach for building comprehensive security systems. Most of the existing material talks about particular security breaches or security holes and their remedies. After working on security issues for over a year, and having studying the GIAC Level One Security Essentials Certification (GSEC) courseware, I am making an attempt in this paper to document the process and methodology for implementing computer security based in corporate networks.