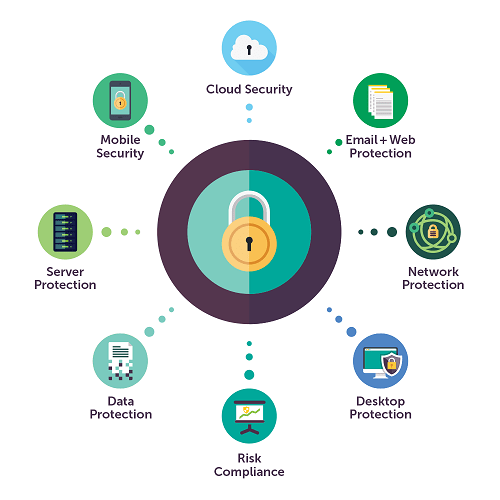
Endpoint Security Solutions
Endpoint security solutions include data security, network security, advanced threat prevention, forensics and remote access VPN for complete endpoint protection.
Endpoint Security is a centralized approach to protecting all endpoints - servers, desktops, laptops, smartphones and other devices - connected to the corporate IT network from cyber threats. This methodology enables efficient, effective and easier security management. Some vendors offer Endpoint Security systems that includes antivirus, firewall and other high defined security software.
When any device-smartphone, laptop, tab etc- is connected remotely to a network, the endpoint thus created would provide an entry point for threats and malware. Endpoint security is all about adequately securing such endpoints and thereby securing a network by blocking access attempts and such risky activities at endpoints.
Today, as more enterprises adopt practices like BYOD and also as incidences of mobile threats are consistently on the rise, endpoint security becomes highly relevant. Employees today connect to company networks using their laptops or mobile devices, from their homes and also while on the move. In this scenario, when security perimeters tend to be undefinable and ever-shifting, a centralized security solution won't be adequate. It's here that endpoint security comes in, supplementing centralized security measures with additional layers of protection at endpoints, which are not just entry points for threats aThe Endpoint Security Solutions works on a client-server model. Within the network there would be the security software, located on a centrally managed and accessible server or gateway. On each endpoint or endpoint device would be located the client software. The security software authenticates logins made from the endpoints and simultaneously updates client software when needed.nd attacks, but points of egress for sensitive data (corporate and personal) as well.
Companies need to ensure that endpoint devices meet security standards; this has to be ascertained before such devices are granted network access. Endpoint security helps enterprises maintain greater control over all access points and also helps block threats and access attempts effectively. Endpoint security tools also help monitor for, detect and block malicious activities.
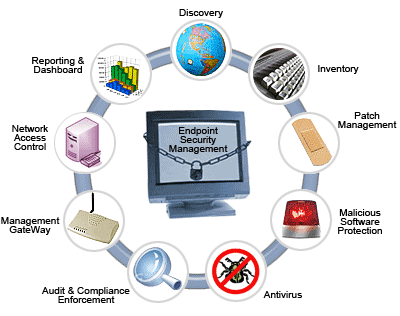
An endpoint security system typically consists of a centrally located security software (which is located on a centrally managed server or gateway within the network) plus the client software that's installed on each endpoint or endpoint device.
What is the difference between Endpoint Security and Antivirus Software?
It's to be understood that endpoint security software happens to be basically different from the antivirus software. In the case of endpoint security software, it's not an individual device that's protected; it's the network as a whole that is secured. The endpoints or endpoint devices, on the other hand, bear some amount of responsibility for their own security as well. This means that even when there is an endpoint protection software to safeguard a network, it's always necessary also to protect endpoint devices like laptops, smartphones etc with antivirus or antimalware tools.
Endpoint Security Solutions also works as a SaaS (Software-as-a-Service) model; here the security programs and the host server are both maintained remotely by the merchant.
How Does Endpoint Security Solutions work?
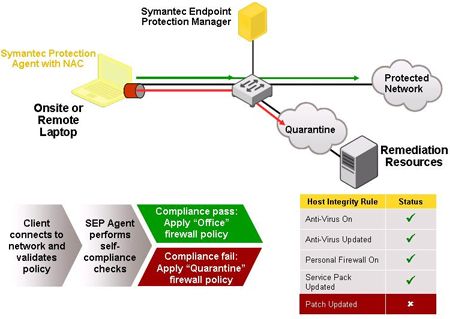
The Endpoint Security Solutions works on a client-server model. Within the network there would be the security software, located on a centrally managed and accessible server or gateway. On each endpoint or endpoint device would be located the client software. The security software authenticates logins made from the endpoints and simultaneously updates client software when needed.
Endpoint Security Solutions also works as a SaaS (Software-as-a-Service) model; here the security programs and the host server are both maintained remotely by the merchant.
Why Endpoint Protection is so important today
An endpoint is always a potential entry point for threats. Endpoint devices, including smartphones, laptops, tablets can be used by cyber criminals to attack networks with malware that could help them steal data from the network systems. Today, the risk is even bigger as enterprises all over the world adopt practices like BYOD (Bring Your Own Device) and personal devices- smartphones, tablets etc- are connected to enterprise networks. Mobile threats have shown an increasing trend in recent times. People even connect to organizational networks using their home computer. In such a scenario endpoint security gains significance since it supplements centralized security solutions with additional protection and prevents threats to secure the network. Endpoint devices would need to meet security standards before being granted network access; this would help prevent threats to a great extent. Endpoint security software also helps in monitoring endpoints and endpoint devices for risky and malicious activities.